The video extends our previous Cisco ISE 1.3 posture assessment to remote VPN users. The goal is to have our VPN user subject to the same set of posture checks to enforce consistent network access experience regardless of user locations. Using the same posture policies with ClamWin Antivirus, we will concentrate on configuration on ASA, and authorization policy on ISE to support remote VPN. Configure ISE 2.0 and Encrypt AnyConnect 4.2 Posture BitlLocker Encryption Configure Remote Access VPN on FTD Managed by FDM Configure SSL Anyconnect With ISE Authentication And Class Attribute For Group-Policy Mapping. The Implementing and Configuring Cisco Identity Services Engine (SISE) Class shows you how to deploy and use Cisco® Identity Services Engine (ISE), an identity and access control policy platform that simplifies the delivery of consistent, highly secure access control across wired, wireless, and VPN connections. A VPN, or Virtual Private Network, is a way for individuals and companies to protect your personal data and identities. VPNs are used to block your IP address and redirect it somewhere else. This is useful for blocking parties from tracking your data and browsing habits or viewing websites or services that may not be available in your area.
How to update AnyConnect & Compliance Modules on Cisco Identity Services Engine (ISE)
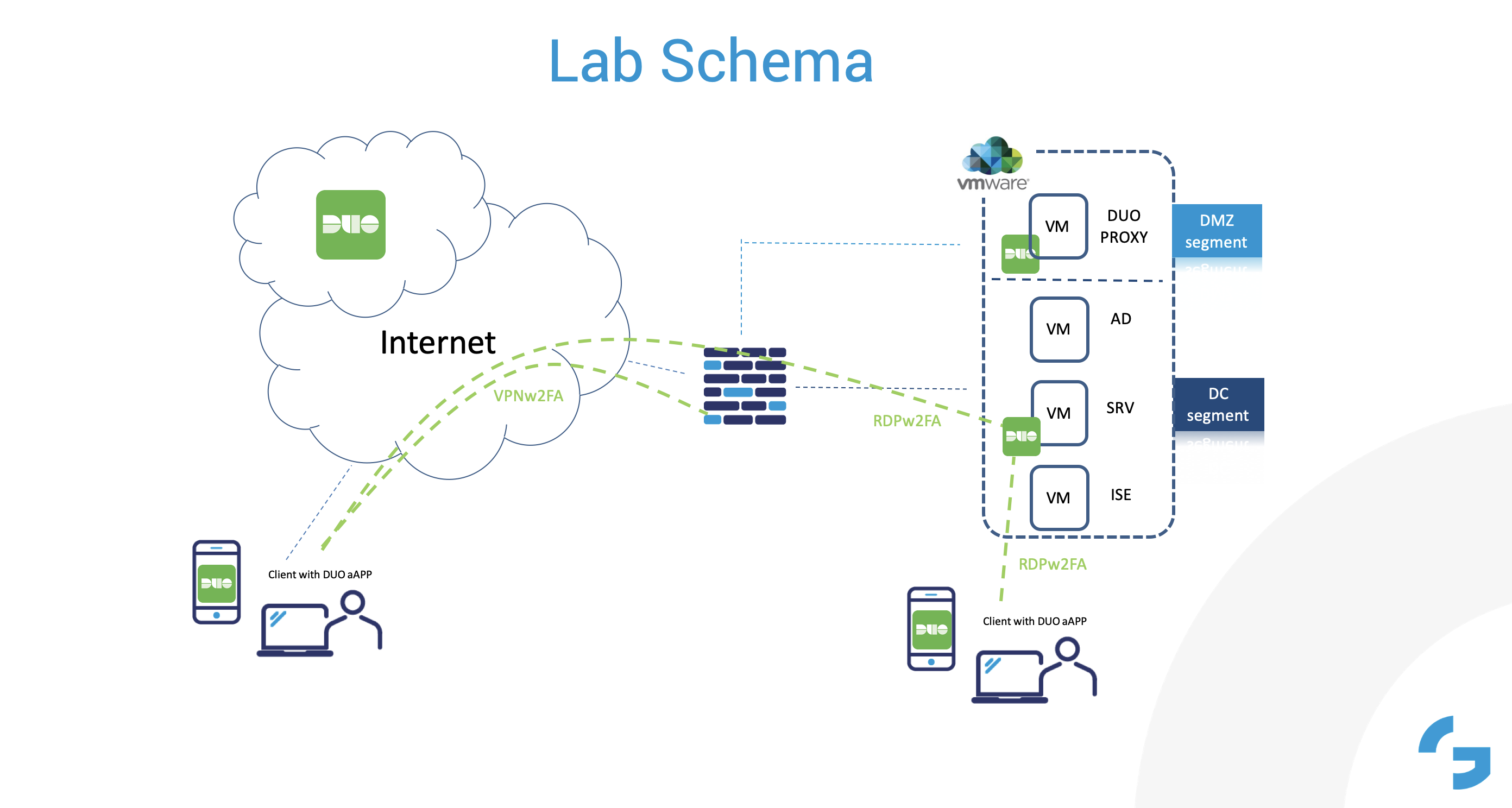
I've recently had the pleasure of deploying Cisco's Identity Service Engine (ISE) as an integrated security solution for a customer. Part of the ISE deployment involved configuring determining the security posture for VPN-connected clients, prior to allowing the client node access to the corporate network.
In order for VPN posturing to work on the ASA firewall, there is an additional compliance module that must be installed on the ASA. The Compliance Module (aka ISE Posture Module) is part of the AnyConnect Secure Mobility Client and offers the Cisco AnyConnect Secure Mobility Client the ability to assess an endpoint's compliance for things like antivirus, antispyware, and firewall software installed on the client endpoint.
In our lab environment, we deployed the windows version of the compliance module on our Cisco ASA firewall. See diagram below:
It is crucial that the Client Provisioning Policy within ISE references the appropriate version of both the AnyConnect and Compliance packages that are deployed on the ASA firewall. Vanderlee plug-ins. I've seen instances where the VPN posture module does not work correctly due to the version mismatch between ISE and the ASA firewall and where the posture check does not kick off while the client endpoint is attempting to connect via VPN to the corporate network.
Setup Folder Name: WondershareFilmora9.2.9.13x64Multilingual.zip; Full Setup Size: 256 MB, ( Recommended 2 GB) Setup Type: Offline Installer or Full Standalone Setup; Compatibility: 32Bit(x86),64 Bit (x64) Developed by: Wondershare Filmora; System Requirements for the Software: Operating System: Windows XP/Vista/7/8/8.1/10. Wondershare Filmora (Filmora Version X for Windows) is an easy and powerful video editing software to edit & personalize videos with rich music, text, filter, element. Download Filmora and try. Empower your imagination with Filmora, an easy-to-use video editor with powerful tools. 9.2.0.31 01 August 2019 Setup. 270 MB: 9.0.1 Dec.11, 2018 Setup. Good Day Admin, I am using filmora 9.2.0.35 with a total of 34 effects packs (downloaded from a persian website, i am not sure if i'm supposed to mention the name here). The application is installed in C:Program files, will your your effects packs work with an. Filmora Video Editor is a powerful video editing tool for Windows users. It was originally called Wondershare Video Editor but was rebranded as Filmora after its fifth release. Some of the key features offered by the video editor are animation, overlays, audio control, on-screen recording, and multi-editing modes. The video editor is popular for its feature-rich but straightforward interface. Filmora 9.2 1 setup windows 10. Download Wondershare Filmora 9.2.1.10 full Crack – Hello, welcome back to the site encrack.com, as usual to re-post this time about Download Wondershare Filmora 9.2.1.10 with keygen, Download Wondershare Filmora 9.2.1.10 Full Version This application is allows you to cut, edit, merge, and trim clips. Furthermore you will able to add your favorite music dircectly.
Unfortunately, while the ISE administrator can edit the Compliance Module version under the AnyConnect Agent Configuration, the AnyConnect Package CANNOT be edited. To align the AnyConnect Agent Configuration versioning name with the AnyConnect Package, I highly recommend on creating a new AnyConnect Agent Configuration.
As far as compatibility between the AnyConnect and Compliance Module is concerned, a quick check of the compatibility matrix indicates that the AnyConnect Secure Mobility Client needs to be 4.x. This support documentation also lists the supported versions of patch-management, anti-virus, anti-malware, etc.
The following steps below details the step-by-step procedure on how to update both the AnyConnect and Compliance Module on the Cisco ISE Policy Administration Node (PAN).
- Update AnyConnect and Compliance Module Packages on Cisco ASA firewall
- AnyConnect and Compliance Module Packages are downloaded from Cisco Online
- Move the firmware to the ASA flash
- Download and install AnyConnect Package on Cisco ISE
- Policy > Policy Elements > Results > Client Provisioning > Results
- Click Add > Agent resources from local disk:
- Select 'Cisco Provided Packages' and click on the 'Browse' button to upload the package to ISE. Click on the Submit button. Another window will then prompt the ISE administrator to confirm the MD5 hash, click on OK.
- Download and install the AnyConnect Compliance Module (.pkg) on ISE:
- Policy > Policy Elements > Results > Client Provisioning > Results
- Click Add > Agent resources from local disk:
- Select 'Cisco Provided Packages' and click on the 'Browse' button to upload the package to ISE. Click on the Submit button. Another window will then prompt the ISE administrator to confirm the MD5 hash, click on OK.
Once the new AnyConnect and Compliance Modules have been uploaded, a new Posture Profile will need to be created.
Is Vpn And Apn The Same
- Create a new Posture Profile
- Policy > Policy Elements > Results > Client Provisioning > Resources
- Click Add > AnyConnect Configuration
- Select the new AnyConnect Package under the dropdown
- Enter the configuration name. Include the version number in the name - ex 'AnyConnect Configuration 4.5.4029.0'
- Select the new compliance module that was added to ISE in Step #3.
- Under Profile Selection, select 'POSTURE_PROFILE'
- Leave everything else to default and click on the 'Save' button.
The final step is to modify the Client Provisioning Policy to include the new AnyConnect Agent Configuration in ISE.
- Modify the Client Provisioning Policies
- Policy > Client Provisioning
- Edit the Windows rule to include the new AnyConnect Agent Configuration
- Under Results, under Agent, select the new AnyConnect agent that was just created.
- Click on Save and we should be good to go.
Description
Implementing and Configuring Cisco Identity Services Engine (SISE)
Objectives
Among other tasks, after taking this class you should be able to:
~ Describe Cisco ISE deployments
~ Describe concepts and configure components related to 802.1X and MAC Authentication Bypass (MAB) authentication
~ Describe how Cisco ISE policy sets are used to implement authentication and authorization
~ Describe third-party Network Access Devices (NADs), Cisco TrustSec®, and Easy Connect
~ Describe and configure web authentication, processes, operation, and guest services
~ Describe and configure Cisco ISE profiling services, and understand how to monitor these services
~ Describe BYOD challenges, solutions, processes, and portals
~ Configure a BYOD solution
~ Describe the value of the My Devices portal and how to configure this portal
~ Describe endpoint compliance, compliance components, posture agents, posture deployment and licensing, and the posture service in Cisco ISE.
~ Describe and configure TACACS+ device administration using Cisco ISE, including command sets, profiles, and policy sets
~ Migrate TACACS+ functionality from Cisco Secure Access Control System (ACS) to Cisco ISE, using a migration tool

- Select 'Cisco Provided Packages' and click on the 'Browse' button to upload the package to ISE. Click on the Submit button. Another window will then prompt the ISE administrator to confirm the MD5 hash, click on OK.
Once the new AnyConnect and Compliance Modules have been uploaded, a new Posture Profile will need to be created.
Is Vpn And Apn The Same
- Create a new Posture Profile
- Policy > Policy Elements > Results > Client Provisioning > Resources
- Click Add > AnyConnect Configuration
- Select the new AnyConnect Package under the dropdown
- Enter the configuration name. Include the version number in the name - ex 'AnyConnect Configuration 4.5.4029.0'
- Select the new compliance module that was added to ISE in Step #3.
- Under Profile Selection, select 'POSTURE_PROFILE'
- Leave everything else to default and click on the 'Save' button.
The final step is to modify the Client Provisioning Policy to include the new AnyConnect Agent Configuration in ISE.
- Modify the Client Provisioning Policies
- Policy > Client Provisioning
- Edit the Windows rule to include the new AnyConnect Agent Configuration
- Under Results, under Agent, select the new AnyConnect agent that was just created.
- Click on Save and we should be good to go.
Description
Implementing and Configuring Cisco Identity Services Engine (SISE)
Objectives
Among other tasks, after taking this class you should be able to:
~ Describe Cisco ISE deployments
~ Describe concepts and configure components related to 802.1X and MAC Authentication Bypass (MAB) authentication
~ Describe how Cisco ISE policy sets are used to implement authentication and authorization
~ Describe third-party Network Access Devices (NADs), Cisco TrustSec®, and Easy Connect
~ Describe and configure web authentication, processes, operation, and guest services
~ Describe and configure Cisco ISE profiling services, and understand how to monitor these services
~ Describe BYOD challenges, solutions, processes, and portals
~ Configure a BYOD solution
~ Describe the value of the My Devices portal and how to configure this portal
~ Describe endpoint compliance, compliance components, posture agents, posture deployment and licensing, and the posture service in Cisco ISE.
~ Describe and configure TACACS+ device administration using Cisco ISE, including command sets, profiles, and policy sets
~ Migrate TACACS+ functionality from Cisco Secure Access Control System (ACS) to Cisco ISE, using a migration tool
Prerequisite Knowledge Advisory
Before taking this class, you should have the following experience and skills:
~ Familiarity with the Cisco IOS® Software Command-Line Interface (CLI)
~ Familiarity with Cisco AnyConnect® Secure Mobility Client
~ Familiarity with Microsoft Windows operating systems
~ Familiarity with 802.1X
Is Vpn Illegal
Course Duration
5 days instructor-led training with hands-on lab practice.
Exam Required for SISE Certification
This exam certifies your knowledge of Cisco Identity Services Engine, including architecture and deployment, policy enforcement, Web Auth and guest services, profiler, BYOD, endpoint compliance, and network access device administration.
Exm: 300-715 SISE
After you pass your exam you earn the Cisco Certified Specialist – Security Identity Management Implementation certification.
(To complete CCNP Security, you also need to pass the Implementing and Operating Cisco Security Core Technologies (350-701 SCOR).)
SISE Outline
The class outline is as follows:
Lecture:
- Introducing Cisco ISE Architecture and Deployment
- Cisco ISE Policy Enforcement
- Web Authentication and Guest Services
- Cisco ISE Profiler
- Cisco ISE BYOD
- Cisco ISE Endpoint Compliance Services
- Working with Network Access Devices
Ise Vpn Authentication
Labs:
Use Vpn Free
- Access the SISE Lab and Install ISE 2.4
- Configure Initial Cisco ISE Setup, GUI Familiarization, and System Certificate Usage
- Integrate Cisco ISE with Active Directory
- Configure Basic Policy on Cisco ISE
- Configure Policy Sets
- Configure Access Policy for Easy Connect
- Configure Guest Access
- Configure Guest Access Operations
- Create Guest Reports
- Configure Profiling
- Customize the Cisco ISE Profiling Configuration
- Create Cisco ISE Profiling Reports
- Configure BYOD
- Blacklisting a Device
- Configure Cisco ISE Compliance Services
- Configure Client Provisioning
- Configure Posture Policies
- Test and Monitor Compliance-Based Access
- Test Compliance Policy
- Configure Cisco ISE for Basic Device Administration
- Configure TACACS+ Command Authorization
